TryHackMe: Bulletproof Penguin
Bulletproof plugin is an easy room that deals with hardening security on the common services that run on a Linux machine. This room covers services such as FTP, MySQL, Redis, SSH, etc., and how their configurations can be changed to secure them from unauthorized access.

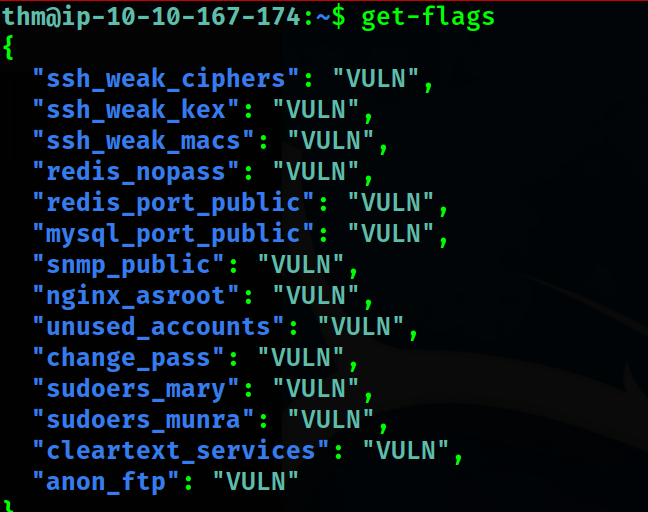
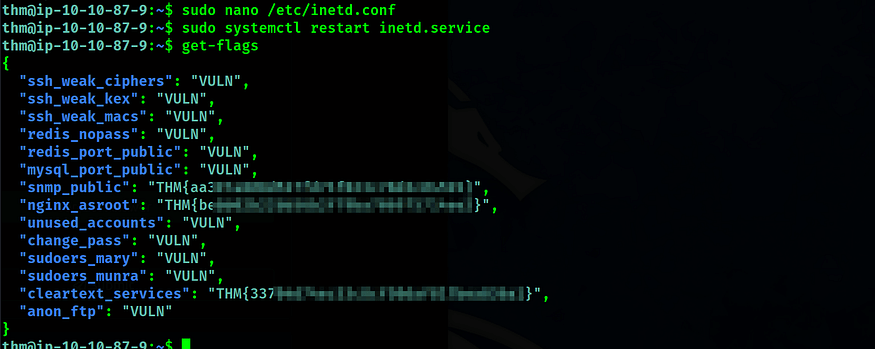
Our goal in each task is to make appropriate changes to the services running to get flags. To get a flag after each task is completed, we need to run the command ‘get-flags’ as shown below.
First, we need to connect to the machine via SSH using the credentials provided to us:
username: thm password: p3ngu1n

Task 1: Redis Server No Password
By running NMAP, we need to find out if Redis is running on the machine.

We can now try to connect to the Redis server. We are being instructed that redis can be accessed without authentication.

As we can see, the requirepass field is blank. Our task is to assign a password to avoid unauthorized access
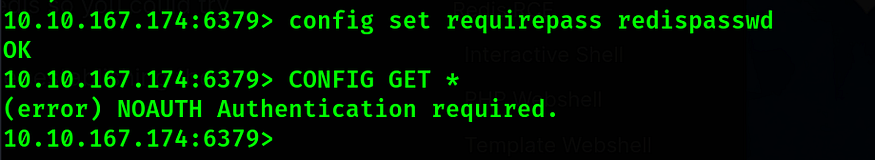
After changing the password, we are asked to authenticate.
For some reason, I was not able to retrieve the flag after making this change. So I decided to change the config file.

We need to restart the service for the changes to take effect.

Task 2: Report Default Community Names of the SNMP Agent
Our task here is to change the community name for the SNMP. Let’s run snmpwalk with using the string public.

Let’s change the string to something hard to guess.


Now, we need to restart the service and get our flag.

Task 3: Nginx Running as Root
Nginx should not be running as root. An attacker can compromise the web server and gain root privileges. The existing www-data account must be used instead which has low privileges.
Our task here is to change the user account from root to www-data.


We will replace the user root with www-data and restart the service.

Task 4: Cleartext Protocols
For this task, we are required to:
- Take down the telnet service
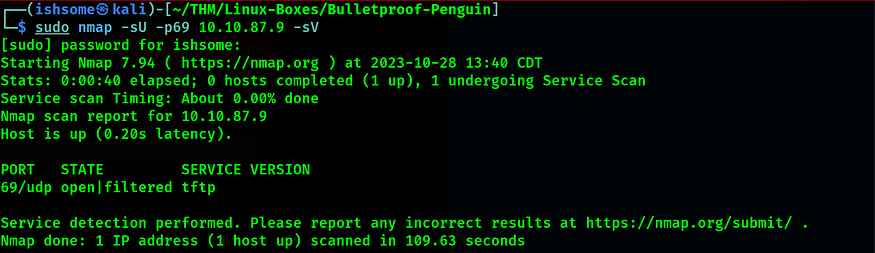
- Take down the service in port 69/udp
Let’s check what is running on port 69.
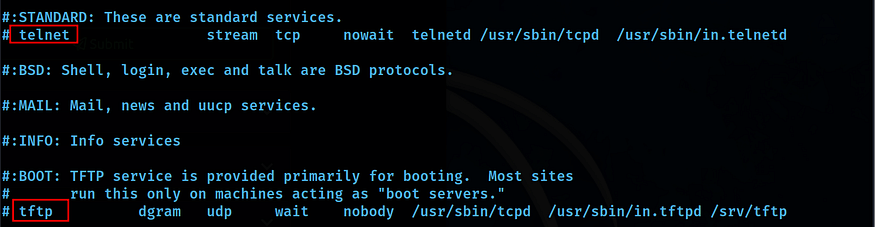
Now we need to disable the telnet and tftp on the server. As can be seen from the below output, we need to make changes to the inetd config file.
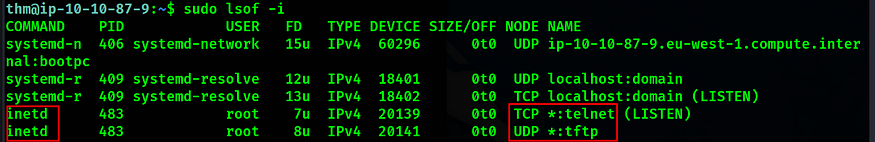
We will just comment on the lines highlighted in the below screenshot
Task 5: Weak SSH Crypto
Our task is to disable all of the reported weak algorithms currently available to the SSH service
- Disable the reported weak KEX algorithm(s)
- Disable the reported weak encryption algorithm(s)
- Disable the reported weak MAC algorithm(s)
diffie-hellman-group1-sha1
3des-cbc
aes128-cbc
aes256-cbc
hmac-md5–96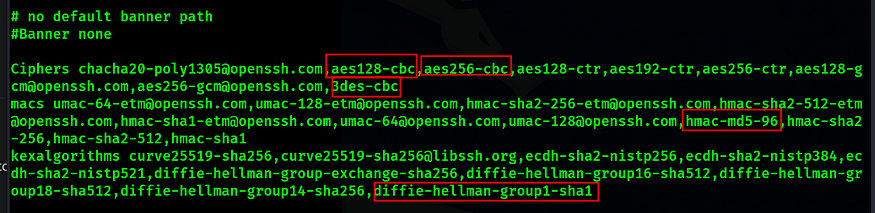
After removing the highlighted items from the configuration file, we will restart the service.

Task 6: Anonymous FTP Logging
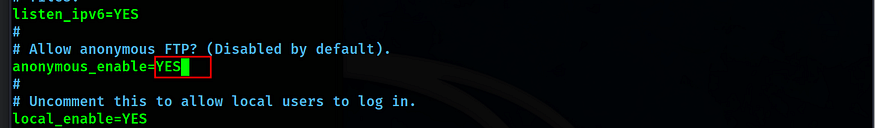
Our goal here is to disable Anonymous login via FTP on the machine. To do this we will need to edit the vsftpd configuration file. All we need to do is change the Value from YES to NO.
Task 7: Weak Passwords
In this task, we need to make the following changes:
- Change passwords for users mary and munra to something complex so that it is hard to guess and not not easily brute-forced
- Remove accounts joseph and test1
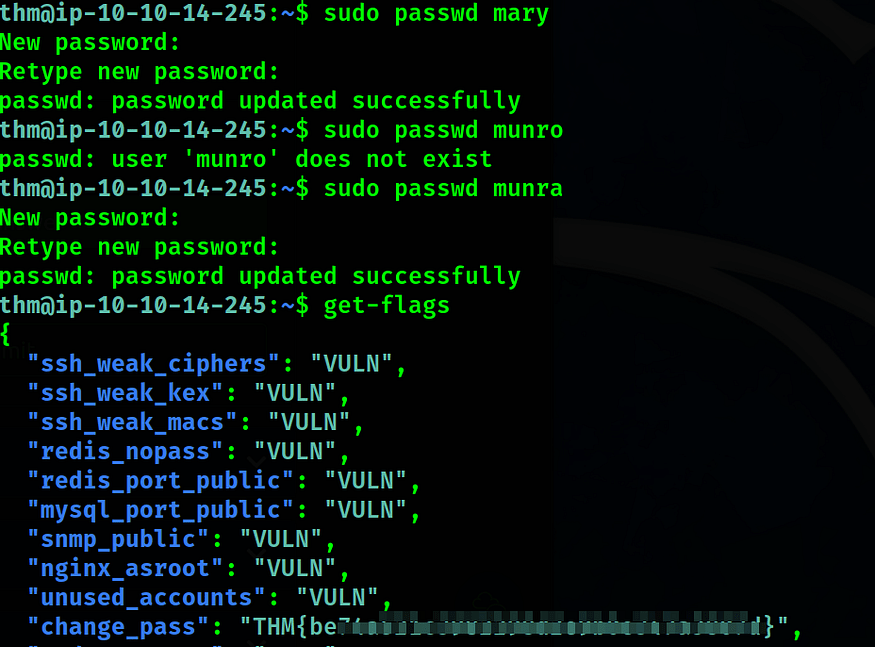
Next, we will delete the accounts from the machine
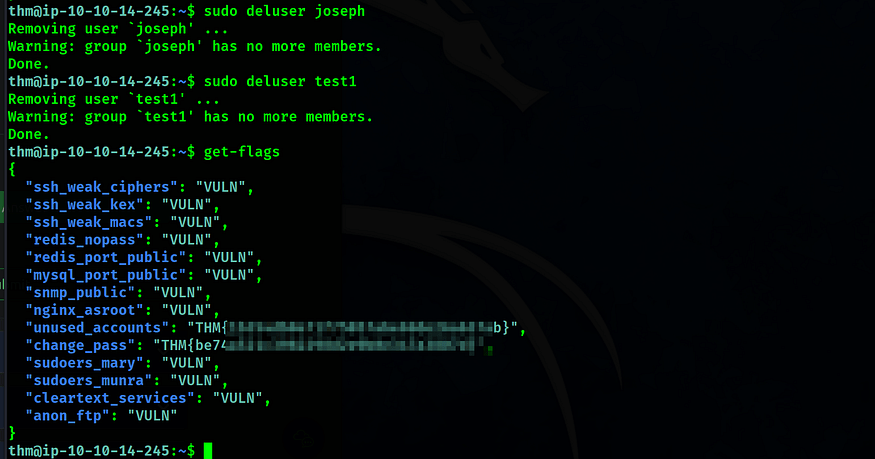
Task 8: Review SUDO Permissions
Here, we are required to do the following tasks:
- Revoke all sudo privileges from user munra.
- The user mary must be able to run the /usr/bin/ss command as root. When doing so, she must NOT be asked for her password. Assign the corresponding sudo privileges.
To revoke munra’s SUDO privileges, we need to comment out the highlighted line. And add a line (see below screenshot) to give mary SUDO permissions on /usr/bin/ss binary.
It is very important that we use the below command to make changes. Also, we need to make sure the syntax we are using to add anything to the file is correct otherwise it will break the file and can cause a lot of problems.
sudo visudo

To verify, you can try running the binary as sudo while logged in as mary.

Task 9: Exposed Database Ports
In this task, we are required to:
1. Modify the MySQL’s service configuration to bind port 3306 to 127.0.0.1 (localhost) only
2. Modify the Redis’ service configuration to bind port 6379 to 127.0.0.1 (localhost) only
First, let’s change the bind-address in the MySQL config file to local host only.sudo nano /etc/mysql/mysql.conf.d/mysqld.cnf
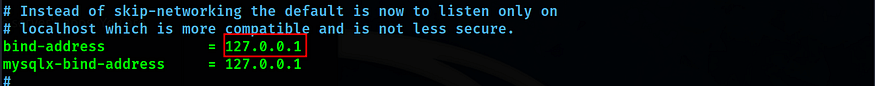
Now, we can restart the sshd.service and fetch our flag
Next, we need to make the same change to the Redis configurationsudo nano /etc/redis/redis.conf

Restart the redis service to get the final flag

We may know how to abuse these misconfiguration but at the same time, we also need to know how to fix them. This room clearly showcases how a simple misconfiguration can lead to the compromise of the machine, how a simple change can prevent unauthorized access, and why managing system user accounts regularly is so important.
Hope you liked this walkthrough. Thanks for reading 🙂
Leave a Reply